[Mains Static] Challenges to Internal Security through Communication Networks

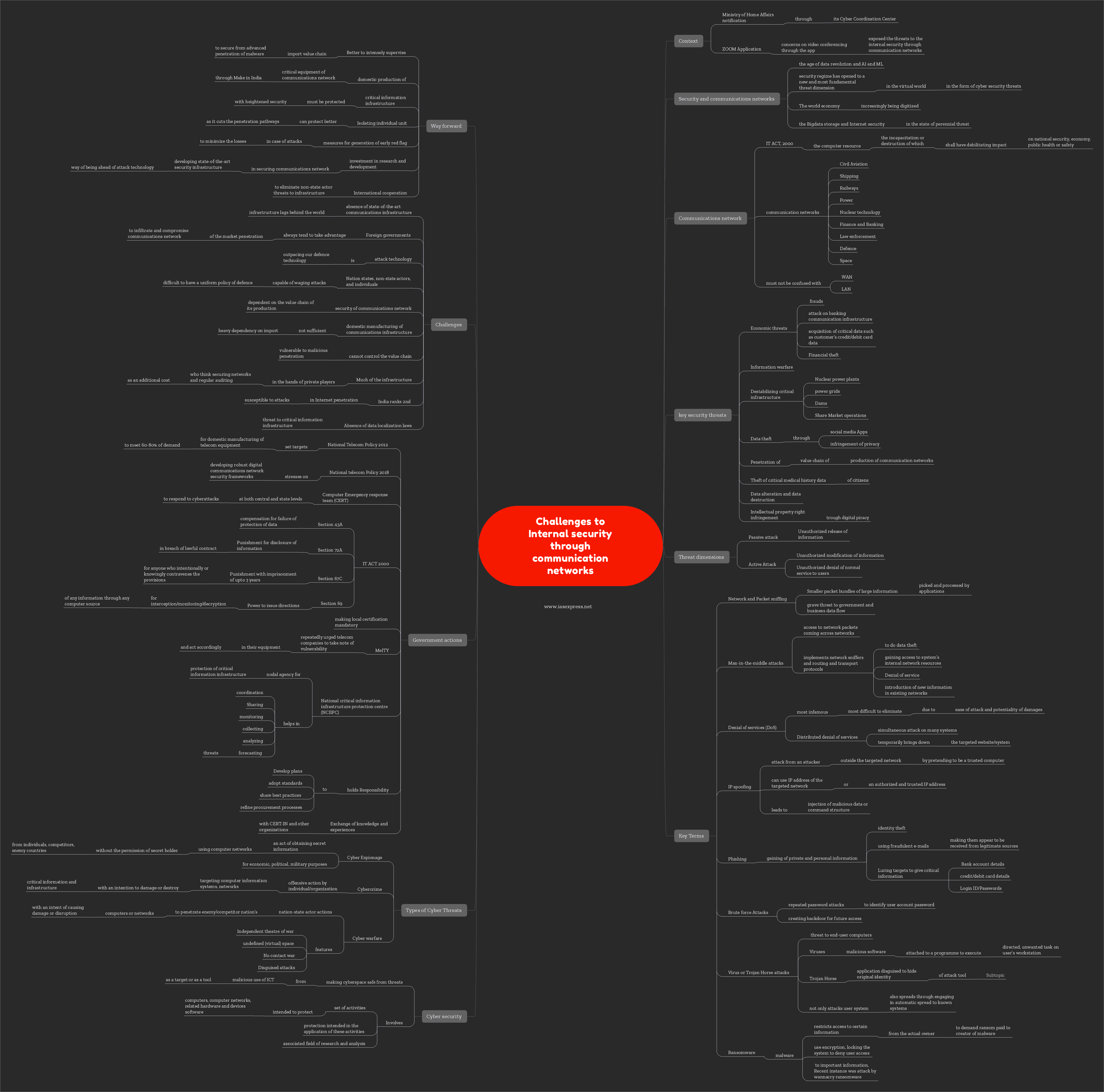
Context
The Ministry of Home Affairs notification through its Cyber Coordination Center on ZOOM Application after Computer Emergency Response Team’s (CERT-IN) raised concerns on video conferencing through the app in lockdown situation once again exposed the threats to the internal security through communication networks.
Security and Communication Networks
In the age of data revolution and AI and ML, the security regime has opened to a new and most fundamental threat dimension in the virtual world in the form of cybersecurity threats and the safety of the use of communication networks. The world economy is increasingly being digitized and the bigdata storage and internet security are in the state of the perennial threat of attacks.
What are communication Networks?
Communication networks are defined as “the computer resource, the incapacitation or destruction of which, shall have a debilitating impact on national security, economy, public health or safety” in the IT Act, 2000. They form a part of our critical information infrastructure.
The communication networks are crucial to the critical infrastructure connectivity such as
- Civil Aviation
- Shipping
- Railways
- Power
- Nuclear technology
- Finance and Banking
- Law enforcement
- Defence
- Space etc.
Communication networks must not be confused with computer networks such as WAN, LAN, etc. because they are merely one form of communication network.
What are the Key Security threats to communication networks?
The major security threats to communications network can take the form of the following ways
- Economic threats such as frauds, attack on banking communication infrastructure, acquisition of critical data such as customer’s credit/debit card data, Financial theft to destabilize the economy
- Information warfare
- Destabilizing critical infrastructure like Nuclear power plants, power grids, Dams, Share Market operations through cyber attacks. g. Stuxnet’s alleged involvement in destabilizing Iran’s Nuclear programme.
- Data theft through social media applications, infringement of privacy
- Penetrating value chain of production of communications network infrastructure and spying through this penetration
- Theft of critical medical history data of a nation’s citizens
- Data alteration and data destruction on the website and impairing its operations
- Intellectual property right infringement through digital piracy
The threat to communications network can be of following types
- Unauthorised release of information- called Passive attack
- Unauthorised modification of information- Active attack
- Unauthorised denial of normal service to users-Active Attack
Explanation of Key Terms
- Network and Packet sniffing
Smaller packet bundles of large information are picked and processed by applications through “off-network”. This kind of application that interprets the network packets is called packet sniffers. This poses a grave threat to government and business data flow.
- Man-in-the-middle attacks
It refers to access to network packets coming across networks. It implements network sniffers and routing and transport protocols to do data theft, gaining access to the system’s internal network resources, Denial of service, the introduction of new information in existing networks to manipulate the system.
- Denial of services (DoS)
This is the most infamous attack among attacks on communication networks and most difficult to eliminate. The ease of attack and potentiality of damages make them an important threat that deserves special attention.
Distributed denial of services attack refers to a simultaneous attack on many systems which temporarily brings down the targeted website/system.
- IP spoofing
IP spoofing is an attack from an attacker outside the targeted network by pretending to be a trusted computer. It can use the IP address of the targeted network or an authorized and trusted IP address.
It leads to the injection of malicious data or command structure in the existing communication networks between clients.
- Phishing
It refers to gaining private and personal information for identity theft, using fraudulent e-mails making them appear to be received from legitimate sources. Luring targets to give critical information such as Bank account, credit card details, Login ID, and passwords.
- Brute force attacks
The repeated password attacks to identify user account passwords and creating a backdoor for future access.
- Virus or Trojan Horse attacks
Viruses and trojan horse applications are a threat to end-user computers.
Viruses are malicious software attached to a programme to execute a directed, unwanted task on the user’s workstation. Trojan horse is an application disguised to hide the original identity of attack tools. It not only attacks the user system but also spreads through engaging in automatic spread to known systems.
- Ransomware
It is a type of malware that restricts access to certain information from the actual owner to demand a ransom paid to the creator of malware. They use encryption, locking the system to deny user access to important information. A recent instance was the attack by WannaCry ransomware.
From the above discussion, it might have been clear that in the digital world challenges to communication network is mainly challenges in the cyberspace. Cyberwarfare is the new age warfare that doesn’t require physical presence but paralyzes the systems through cyber attacks. Mind you, the virtual attacks can be far more destructive than the mere collapse of physical infrastructure. Cyberspace has actually become the fifth theatre of warfare after land, air, water, and space.
What are the types of cyber threats?
- Cyber Espionage
It is an act of obtaining secret information using computer networks without the permission of secret holders from individuals, competitors, enemy countries for economic, political, military purposes. In 2009, PMO was an alleged victim of cyber espionage by chines hackers.
- Cybercrime
Cybercrime is an offensive action by individuals/organization targeting computer information systems, networks with an intention to damage or destroy critical information and infrastructure.
According to NCRB, the instances of cybercrimes are at an all-time high now due to penetration of communication networks.
- Cyberwarfare
Cyberwarfare are nation-state actor actions to penetrate enemy/competitor nation’s computers or networks with the intent of causing damage or disruption.
What are the features of the cyberwar?
- Independent theatre of war due to the development of the internet and sophisticated communication infrastructure
- An undefined (virtual) space as it is impossible to protect national cyberspace by just controlling and monitoring internet networks inside its territory as cyberspace is truly global.
- It is a No contact war as the attacker does not need to be present at the site of the attack. The malware like Stuxnet can be penetrated in any link of the global value chain of communications infrastructure and then controlling the target can be from distant places.
- Disguised attacks and attackers make it even more dangerous and untraceable and it surely complicates cybersecurity policy.
What is cybersecurity?
Cybersecurity is making cyberspace safe from threats, i.e. cyber-threats. “cyber-threats” means the malicious use of ICT as a target or as a tool by malevolent actors. It involves three things
- A set of activities, intended to protect computers, computer networks, related hardware, and devices software, and the information they contain and communicate, including software and data, as well as other elements of cyberspace, from all threats, including threats to the national security.
- The protection intended in the application of these activities and measures;
- The associated field of research and analysis, aimed at implementing those activities and improving their quality.
What is the government doing to secure communications network?
- The National Telecom Policy 2012 has set targets for domestic manufacturing of telecom equipment to meet 60 to 80 percent of demand.
- The National Telecom Policy 2018 stresses on developing robust digital communications network security frameworks.
- The Computer Emergency response team (CERT) at both the national and state-level have been formed to respond to cyberattacks.
- IT Act, 2000
- Section 43A- compensation for the failure of protection of data
- Section 72A- Punishment for disclosure of information in breach of lawful contract
- Section 67C- Punishment with imprisonment of up to 3 years for anyone who intentionally or knowingly contravenes the provisions
- Section 69- Power to issue directions for interception/monitoring/decryption of any information through any computer source.
- A number of other measures, such as making local certification mandatory, have been announced.
- The Ministry of Communications and Information Technology has also repeatedly urged telecom companies to take note of vulnerabilities in their equipment and told them they would be held responsible and subject to penalties if the vulnerabilities are not addressed
- National critical information infrastructure protection centre (NCIIPC)-
- It is a national nodal agency for the protection of critical information infrastructure
- It helps in Coordination, sharing, monitoring, collecting, analysing and forecasting threats.
- It holds Responsibility to Develop plans, adopt standards, share best practices and refine procurement processes.
- Exchange of knowledge and experiences with CERT-IN and other organisations is done in order to better coordinate.
What are the challenges in securing communication networks?
- The absence of state-of-the-art communications infrastructure. The communications infrastructure lags behind the world though it has grown leaps and bounds in past decades.
- Foreign governments always tend to take advantage of the market penetration to infiltrate and compromise communications network.
- The attack technology is outpacing our defence technology.
- Nation-states, non-state actors, and individuals all are capable of waging attacks makes it even more difficult to have a uniform policy of defence.
- The security of the communications network is very much dependent on the value chain of its production.
- The domestic manufacturing of communications infrastructure is not sufficient and we are mostly dependent on imports.
- We cannot control the value chain. This makes us vulnerable to malicious penetration.
- Much of the infrastructure is in the hands of private players who think securing networks and regular auditing as an additional cost.
- India ranks 2nd in number of internet users making it vulnerable to cyber-attacks at multiple fronts
- The absence of data localization laws makes India’s critical infrastructure information vulnerable to attacks.
Way forward
- Better to intensely supervise the import value chain of communication equipment to secure from advanced penetration of malware.
- Take measures for domestic production of critical equipment of the communications network through Make in India.
- The critical information infrastructure must be protected with heightened security in the wake of enhanced attacks.
- Isolating individual units can better protect it from potential attacks as it cuts the penetration pathways.
- Better measures for the generation of the early red flag in case of attacks to minimize the loss during the attacks
- Increase investment in research and development in securing communications networks through developing state-of-the-art security infrastructure. It is a way of being one step ahead of attack technology.
- International cooperation to eliminate non-state actor threats to infrastructure. Better communication can minimize misunderstanding caused by disguised attacks.
Practice Question for Mains
Discuss the challenges in securing communications infrastructure. What are the ways to minimize the threats? (250 words)
Read all internal security articles and mindmaps(static & current)
If you like this post, please share your feedback in the comments section below so that we will upload more posts like this.