Chameleon Trojan
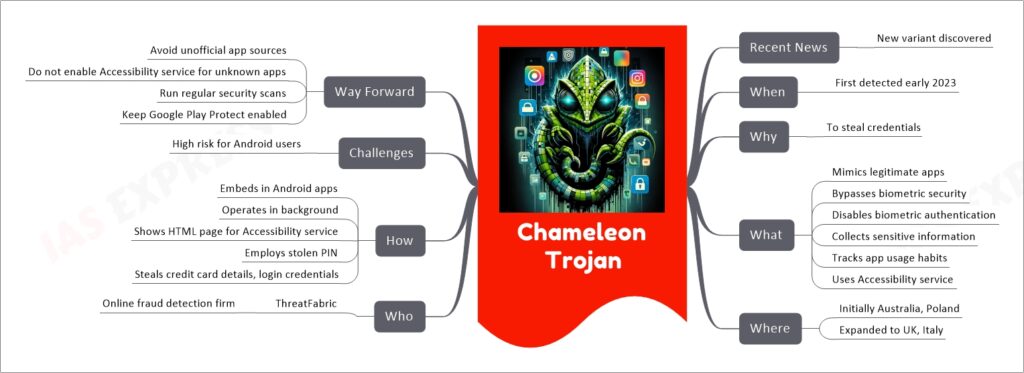
The Chameleon Trojan is a newly identified variant of Android banking malware first detected in early 2023. It’s known for its ability to mimic legitimate apps, thereby bypassing biometric security measures like fingerprint and face unlock to steal phone PINs and other sensitive information. Initially targeting Australia and Poland, its reach has expanded to the UK and Italy. ThreatFabric, an online fraud detection firm, has been closely monitoring this evolving threat. The Trojan operates by embedding itself in legitimate Android apps like Google Chrome, running undetected in the background. It employs various tactics such as using the Accessibility service to gain unauthorized access and employing stolen PINs to unlock devices and steal data like credit card details and login credentials. To protect against this malware, users are advised to avoid unofficial app sources, refrain from enabling the Accessibility service for unknown apps, run regular security scans, and keep Google Play Protect enabled.
If you like this post, please share your feedback in the comments section below so that we will upload more posts like this.